Peer Review
I am making my software available for peer review. This will include the source code, the methods, ways for you to test just one process or test them all, and it will provide save files after each step so you can attempt to decrypt at various stages as part of your peer review.
You are required to accept the Software License before you can gain access to the zipped file. I reserve all rights and this is purely for the purposes of peer review.
Specifically I make the following claims:
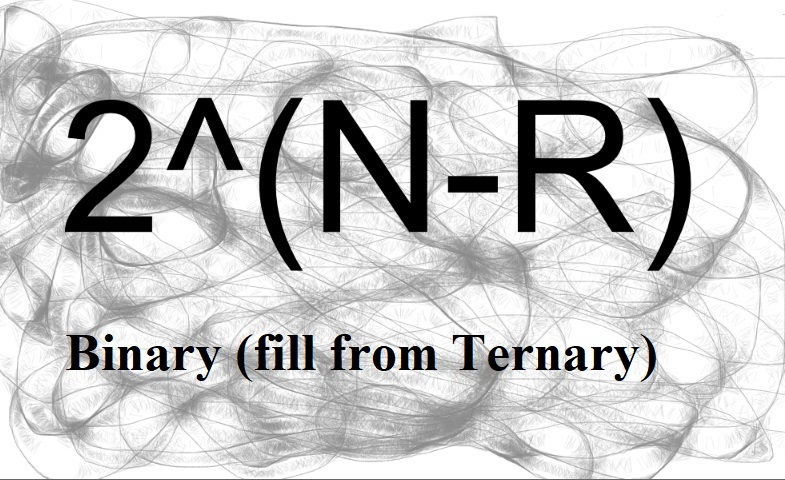
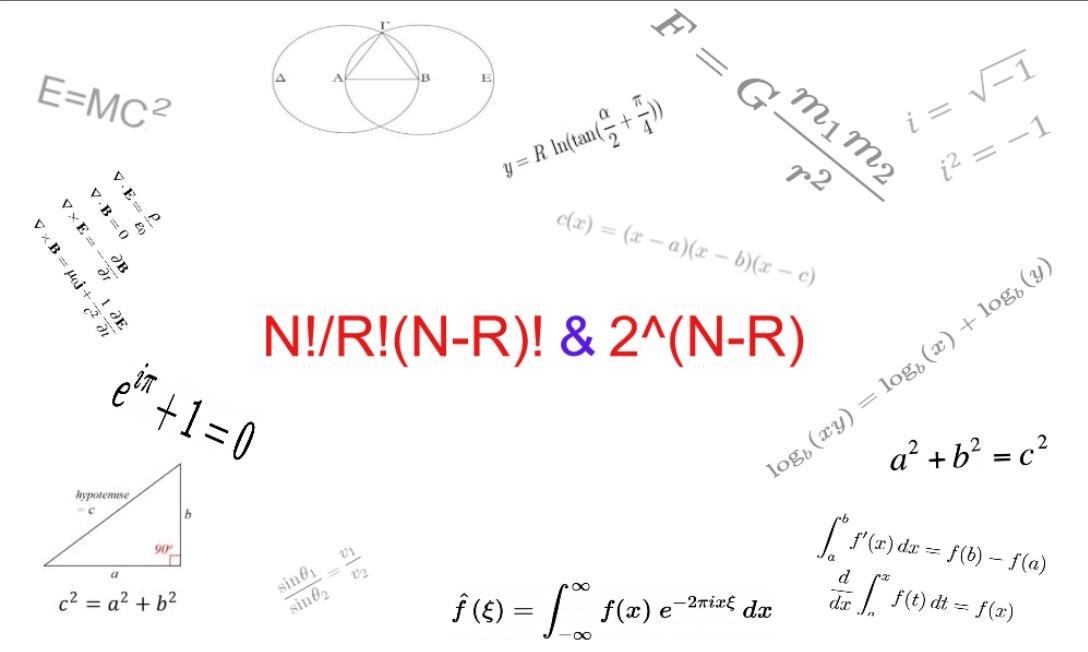
1) A new mathematical method bridging Combinations and Binary/Ternary.
2) A lower number of steps to encrypt and decrypt using the key.
3) Significantly better encryption than AES regarding formula based attacks.
4) Significantly better encryption than AES regarding Brute Force Attacks.
5) More adaptability for increasing the difficulty than AES within the structure.
6) A smaller key than AES uses will result in greater protection.
7) Two NP-Complete mathematical methods are being used to encrypt the data
8) Lossless Encryption
9) The methods involved are novel and new
10)It is possible to have two languages running/stored in a third language (Binary+Combinations in a Ternary Base).
I am seeking peer review of my Combary™ Encryption System and am submitting software, methods, the ability to test individual Processes, see Process after Process changes, input the key, input the data, and am allowing a limited right (see license agreement) to modify and test the software as needed for a full peer review.
License Agreement